
WatchGuard Threat Detection and Response
Network and Endpoint Threat Correlation
Hackers are designing malware to be more sophisticated than ever. Through packing, encryption, and polymorphism, cyber criminals are able to disguise their attacks to avoid detection. Zero day threats and advanced malware easily slip by antivirus solutions that are simply too slow to respond to the constant stream of emerging threats. Organizations of all sizes need a solution that leverages a holistic approach to security from the network to the endpoint. WatchGuard Threat Detection and Response (TDR) is a powerful collection of advanced malware defense tools that correlate threat indicators from Fireboxes and Host Sensors to stop known, unknown and evasive malware threats.
Key Features
- Improves security against advanced malware attacks, including ransomware
- Tight integration with APT Blocker for advanced threat triage
- Correlates network and endpoint insight for enterprise-grade threat visibility
- Works alongside existing antivirus solutions with no impact on endpoint performance
- Scores threats indicators and incidents based on severity to guide response
- Decreases time to detection and remediation through policy-based automation
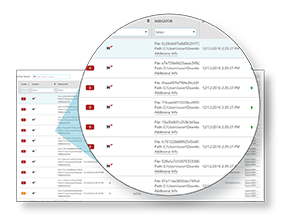
Threat Correlation and Prioritization
ThreatSync is a cloud-based correlation engine that analyzes event data from Host Sensors and Fireboxes to identify malicious behavior. Threats are scored based on severity, for guided remediation.
Threat Visibility on the Endpoint
The lightweight WatchGuard Host Sensor extends threat visibility and management to the endpoint. The WatchGuard Host Sensor continuously sends heuristic and behavioral data from the endpoint up to ThreatSync for correlation and scoring.


Automated Threat Response
TDR provides powerful protection against advanced malware threats and can automatically intervene to quarantine files, kill the processes, or delete registry keys. Mitigate threats as you see them with one click, or by establishing policies for automated response based on the threat score.
Ransomware Prevention with HRP
Host Ransomware Prevention (HRP) is a ransomware-specific module within TDR that uses behavioral analysis and honeypots to look for signs of ransomware. If malware is detected, HRP automatically intervenes to stop the ransomware before files are lost.


Advanced Threat Triage with APT Blocker
Malware is constantly evolving and suspicious indicators could be early warning signs of yet-to-be-identified malware. Now, thanks to tight integration with WatchGuard APT Blocker, suspicious files can be sent for deep analysis and re-scoring in a next-generation cloud-sandbox.
Enterprise-grade Threat Intelligence
Threat Intelligence was previously only a benefit available to enterprise organizations with big budgets and even bigger security teams. With Threat Detection and Response, WatchGuard aggregates and analyzes threat intelligence feeds - delivering the security benefits without passing on the associated complexities or cost.


Additional Security Layer to Existing Antivirus Solutions
Threat Detection and Response doesn’t require users or Managed Security Service Providers (MSSPs) to replace existing AV solutions already deployed. TDR works in tandem with existing AV, bringing an additional, powerful layer of threat detection and event correlation to catch anything that AV might miss.
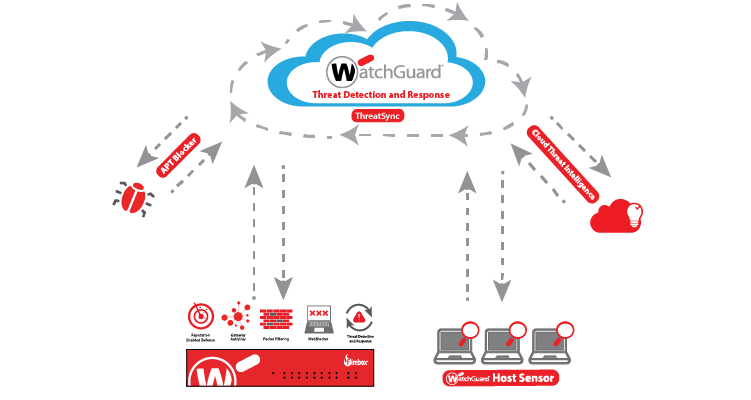
How It Works
Threats detected on the Firebox or via the Host Sensor are sent to ThreatSync, where they are continuously correlated and analyzed, then scored and ranked by severity. Threats can then be quickly remediated through one-click response options, or by leveraging policies to enable an automated response including quarantine the file, kill the process, and delete the registry key persistence.
Documentation:
Download the Host Sensor Datasheet (PDF).
Pricing Notes:
- Pricing and product availability subject to change without notice.

